RECENT ARTICLES
Backdoor accounts discovered in 29 FTTH devices from Chinese vendor C-Data | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentTwo security researchers said this week that they found severe vulnerabilities and what appears to be intentional backdoors in the firmware of 29 FTTH OLT devices from popular vendor .FTTH stands for Fiber-To-The-Home, while OLT stands for Optical Line Termination.The term FTTH OLT refers to networking equipment that...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentTwo security researchers said this week that they found severe vulnerabilities and what appears to be intentional backdoors in the firmware of 29 FTTH OLT devices from popular vendor .FTTH stands for Fiber-To-The-Home, while OLT stands for Optical Line Termination.The term FTTH OLT refers to networking equipment that...WW…
Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentMore than 100,000 Zyxel firewalls, VPN gateways, and access point controllers contain a hardcoded admin-level backdoor account that can grant attackers root access to devices via either the SSH interface or the web administration panel. The backdoor account, discovered by a team of Dutch security researchers from Eye...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentMore than 100,000 Zyxel firewalls, VPN gateways, and access point controllers contain a hardcoded admin-level backdoor account that can grant attackers root access to devices via either the SSH interface or the web administration panel. The backdoor account, discovered by a team of Dutch security researchers from Eye...WW…
2FA bypass discovered in web hosting software cPanel | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentSecurity researchers have discovered a major security flaw in , a popular software suite used by web hosting companies to manage websites for their customers. The bug, discovered by security researchers from Digital Defense, allows attackers to bypass two-factor authentication (2FA) for cPanel accounts. Also:These...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentSecurity researchers have discovered a major security flaw in , a popular software suite used by web hosting companies to manage websites for their customers. The bug, discovered by security researchers from Digital Defense, allows attackers to bypass two-factor authentication (2FA) for cPanel accounts. Also:These...WW…
Hacker leaks passwords for 900+ enterprise VPN servers | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentA hacker has published today a list of plaintext usernames and passwords, along with IP addresses for more than 900 Pulse Secure VPN enterprise servers. Also: ZDNet, which obtained a copy of this list with the help of threat intelligence firm , verified its authenticity with multiple sources in the cyber-security...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentA hacker has published today a list of plaintext usernames and passwords, along with IP addresses for more than 900 Pulse Secure VPN enterprise servers. Also: ZDNet, which obtained a copy of this list with the help of threat intelligence firm , verified its authenticity with multiple sources in the cyber-security...WW…
Mozilla publishes official Firefox anti-tracking policy | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentVideo: Mozilla chooses Google over Yahoo for US Firefox searchMozilla has published today a detailing its official Firefox anti-tracking policies for the first time. Also: These anti-tracking policies are of Firefox's newly redesigned Enhanced Tracking Protection (or Content Blocking) tracker blocking feature...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentVideo: Mozilla chooses Google over Yahoo for US Firefox searchMozilla has published today a detailing its official Firefox anti-tracking policies for the first time. Also: These anti-tracking policies are of Firefox's newly redesigned Enhanced Tracking Protection (or Content Blocking) tracker blocking feature...WW…
News and Advice on the World's Latest Innovations | ZDNET
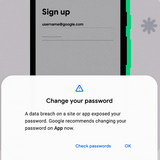
/>The Password Checkup feature will tell Android users when one of their passwords has been exposed in an online data breach.Android users can now take advantage of the Password Checkup feature that Google , the OS maker announced today. On Android, the Password Checkup feature is now part of the "" mechanism, which the OS uses to select text from a cache and fill in forms.The idea is that the Password Checkup feature will take passwords stored in the Android OS password manager and check them against a database containing billions of records from public data breaches and see...…/>The Password Checkup feature will tell Android users when one of their passwords has been exposed in an online data breach.Android users can now take advantage of the Password Checkup feature that Google , the OS maker announced today. On Android, the Password Checkup feature is now part of the "" mechanism, which the OS uses to select text from a cache and fill in forms.The idea is that the Password Checkup feature will take passwords stored in the Android OS password manager and check them against a database containing billions of records from public data breaches and see...WW…

News and Advice on the World's Latest Innovations | ZDNET
Byfor| February 19, 2021 -- 16:02 GMT (08:02 PST)| Topic:The Tor mode included with the Brave web browser allows users to access .onion dark web domains inside Brave private browsing windows without having to install Tor as a separate software package.Added in June 2018, Brave's Tor mode has allowed throughout the years access to increased privacy to Brave users when navigating the web, allowing them to access the .onion versions of legitimate websites like Facebook, Wikipedia, and major news portals.But in this week, an anonymous security researcher claimed they found that...…Byfor| February 19, 2021 -- 16:02 GMT (08:02 PST)| Topic:The Tor mode included with the Brave web browser allows users to access .onion dark web domains inside Brave private browsing windows without having to install Tor as a separate software package.Added in June 2018, Brave's Tor mode has allowed throughout the years access to increased privacy to Brave users when navigating the web, allowing them to access the .onion versions of legitimate websites like Facebook, Wikipedia, and major news portals.But in this week, an anonymous security researcher claimed they found that...WW…
News and Advice on the World's Latest Innovations | ZDNET
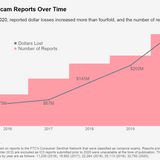
Byfor| February 16, 2021 -- 06:00 GMT (22:00 PST)| Topic:The current COVID-19 pandemic and the subsequent stay-at-home and social distancing directives might have played a major role in romance scams losses reaching record levels in 2020, the US Federal Trade Commission .Here is a step-by-step guide to reducing your digital footprint online, whether you want to lock down data or vanish entirely.Total losses were estimated at a record $304 million, up about 50% from 2019, with the average loss last year being estimated at $2,500 per individual."From 2016 to 2020, reported total dollar...…Byfor| February 16, 2021 -- 06:00 GMT (22:00 PST)| Topic:The current COVID-19 pandemic and the subsequent stay-at-home and social distancing directives might have played a major role in romance scams losses reaching record levels in 2020, the US Federal Trade Commission .Here is a step-by-step guide to reducing your digital footprint online, whether you want to lock down data or vanish entirely.Total losses were estimated at a record $304 million, up about 50% from 2019, with the average loss last year being estimated at $2,500 per individual."From 2016 to 2020, reported total dollar...WW…
News and Advice on the World's Latest Innovations | ZDNET
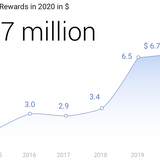
/>Sum is up from the $6.5 million the company paid security researchers a year before, in 2019.Google said today it paid more than $6.7 million in bug bounty rewards to 662 security researchers across 62 countries for submitting vulnerability reports in Google products last year. The figure, up from the $6.5 million the company paid in 2019, is the company's largest prize pool paid to security researchers to date.Most of last year's bug prizes were awarded in the Chrome VRP (Vulnerabilities Rewards Program), which handed out more than $2.1 million to security researchers for 300 bugs...…/>Sum is up from the $6.5 million the company paid security researchers a year before, in 2019.Google said today it paid more than $6.7 million in bug bounty rewards to 662 security researchers across 62 countries for submitting vulnerability reports in Google products last year. The figure, up from the $6.5 million the company paid in 2019, is the company's largest prize pool paid to security researchers to date.Most of last year's bug prizes were awarded in the Chrome VRP (Vulnerabilities Rewards Program), which handed out more than $2.1 million to security researchers for 300 bugs...WW…
Windows XP leak confirmed after user compiles the leaked code into a working OS | ZDNET
We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentThe Windows XP and Windows Server 2003 source code that was has been confirmed to be authentic after a YouTube user compiled the code into working operating systems. Shortly after the leak occurred last week, ZDNet reached out to multiple current and former Microsoft software engineers to confirm...…We and our partners use cookies to understand how you use our site, improve your experience and serve you personalized content and advertising. Read about how we use cookies and your choices . By continuing to use this site, you accept these cookies.AcceptRejectUpdate ConsentThe Windows XP and Windows Server 2003 source code that was has been confirmed to be authentic after a YouTube user compiled the code into working operating systems. Shortly after the leak occurred last week, ZDNet reached out to multiple current and former Microsoft software engineers to confirm...WW…